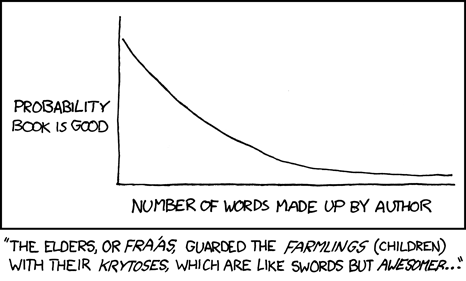
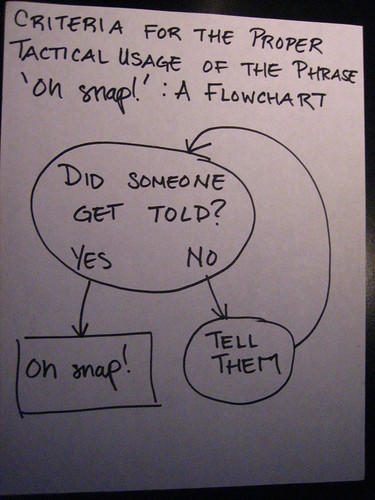
30 November 2008
Bootstraping Problem
I'd say it presents a bit of a bootstrapping problem, depending on how it is packaged or how it is presented to you.
14 November 2008
So Many Failed Banks, So Little Time
Charter Communications Stupidity
Thank you for choosing Charter Chat Live! A Customer Care representative
from Cable TV Order Inquiries will be with you shortly.
You have been connected to CVH Robert S .
Christopher Arnold: Hello?
CVH Robert S : My name is Robert. Thank you for contacting Charter Communications On-line Sales. How may I assist you?
Christopher Arnold: Hello. How are you?
CVH Robert S : ok
CVH Robert S : How may I assist you?
Christopher Arnold: Very good. I was hoping to determine if a better pricing plan exists for the services we currently have. Cable "Big Value" + Internet.
CVH Robert S : To get into a new promo you would need to upgrade your services.
Christopher Arnold: How exactly? I'm not sure what would be upgraded.
Christopher Arnold: I'm open to suggestions.
CVH Robert S : May I please have your full name, service address (street address, city, state, and zip code), and telephone number? This is so that I may pull up information for you in your local area.
Christopher Arnold: Heh, wonder why I had to do that before I signed into a chat session with you?
Christopher Arnold: Christopher Arnold/**** Arnold
Christopher Arnold: 257 ****** Road
Christopher Arnold: ******, **
Christopher Arnold: *****
Christopher Arnold: ***.***.****
CVH Robert S : hold please
CVH Robert S : The lowest house # in our system is 299
Christopher Arnold: That's a nice house down the street. I'd be happy to move there.
CVH Robert S : I would have to fill out a serviceability form to have a tech go out and check to see if the address is serviceable or not, this process takes about 3 to 5 business days.
Christopher Arnold: Uh...OK. I guess I'll just continue watching my existing Charter cable TV and using Charter network services until then.
Christopher Arnold: If it would help for me to move down the street, it really is a nice house. I don't think they would mind too much.
Christopher Arnold: Wow...1-298 ***** must be pretty pissed right now. Glad I'm not them. Wait...I am one of them.
Christopher Arnold: Hello?
CVH Robert S : I can not find your address in our system, can I have your account#?
Christopher Arnold: **** ** *** *******
CVH Robert S : found it
Christopher Arnold: Can I still move to 299 ***** Road? They have an in-law apartment.
CVH Robert S : Can you verify the last 4 of the SS# that is on your account please?
Christopher Arnold: ****
CVH Robert S : That is not the last 4 on the account.
Christopher Arnold: **** my spouse. **** me, if that helps.
CVH Robert S : The account is not in your name Christopher
CVH Robert S : You are not listed as an authorized user.
Christopher Arnold: ****, my spouse.
Christopher Arnold: I'm not listed as an authorized user? Like, I can't watch TV or play around on the computer?
CVH Robert S : No, I can not discuss the account with you.
Christopher Arnold: So you need to chat with my spouse?
CVH Robert S : She will need to chat in her self.
Christopher Arnold: OK, let me get her.
CVH Robert S : Thank you for choosing Charter Communications Chat Support. For general self-help, please visit http://support.charter.com. Also, check out our "Live it with Charter" customer rewards program. It is absolutely free, and you are eligible simply by being a Charter customer! You receive points based on your monthly service rate! For more information and to sign up, you can check out the Live it with Charter website here: http:// www.liveitwithcharter.com Thank you once again, and have a wonderful day!
If you require further assistance, go to www.charter.com/contact
Your session has ended. You may now close this window.
This painful ordeal took approximately 25 minutes and the f*%$er disconnected.
It's not: "We out-source this function to XYZ and you may experience slight lingual, cultural, temporal issues as we adapt to and utilize a global labor market.
It's: "We farm this kind of work out to barnacles scraped from boat hulls that somehow manage to attach themselves to keyboards and THIS is now your perception of our firm, regardless of how many intelligent, considerate or well-spoken individuals we employ or out-source to."
I wonder if those plan changes I made six months ago are actually valid? I should ask....
24 October 2008
15 October 2008
Another Convicted Criminal, Cracker-Turned-"Security Consultant" Profit Story
03 October 2008
29 September 2008
26 September 2008
20 September 2008
16 September 2008
Peer-To-Patent
"The concept behind the program, called Peer-to-Patent, is straightforward: Publish patent applications on the Web for all to see and let anyone with relevant expertise -- academics, colleagues, even potential rivals -- offer input to be passed along to the Patent Office.
By using the power of the Internet to tap the wisdom of the masses, Peer-to-Patent aims to dig up hard-to-find "prior art" -- evidence that an invention already exists or is obvious and therefore doesn't deserve a patent.
The goal is to locate prior art that Patent Office examiners might not find on their own -- and to produce better patents by reducing ones granted on applications that aren't novel. The hope is that this will drive innovation by improving the patent process and reducing the patent infringement lawsuits clogging the courts."
Using the mob to search for prior art and inform the USPTO doesn't seem like a terribly bad idea, so long as it's verifiable through multiple, independent channels or vetting pools (think peer-reviewed academic journals). I'm extremely concerned regarding overly zealous enthusiasm however.
I want to explore this idea but time prohibits me from doing so. To dumb it down, how would a process like the proposed be insulated from a Digg phenomenon as well as an inadvertant data leak that would let a competitor interject itself in the process and, say, stall for time to market?
06 September 2008
More On The Topic Of Alt-Fuel Cool Cars: The Lotus Omnivore
"The Omnivore is a direct injection two-stroke engine with a variable compression ratio system, which means it won't waste fuel and it'll run on just about everything but puppy smiles and children's dreams."
Must...Have....Volvo ReCharge Concept Car
"Picture a gasoline-electric hybrid that's more electric than gasoline. The Volvo ReCharge Concept is just that. Unlike traditional parallel hybrids, which primarily employ internal-combustion engines and electric motors working in tandem, the ReCharge (derived from the sharp new C30 coupe). Is a plug-in serial hybrid — that is to say, there is no mechanical connection between the electric motor drive system and the 1.6-liter four-cylinder gasoline engine. Four in-wheel motors will carry the car up to 100 km (62 miles) on a single charge of the trunk-mounted lithium-polymer batteries (charged from a standard household outlet and boasting, Volvo claims, a life expectancy longer than the car itself). Only when the batteries are fully drained does the engine fire up, spinning a generator which provides juice to the electric motors and recharges the battery. Brilliant."
01 September 2008
American Political Conventions - Terribly Frustrating (Lack Of) Of Use Of Technology
NPR...this is why I no longer listen to you nor sponsor you financially and am close to giving up on PBS.
Irritated. Grrr.....
Has anyone surveyed their constituents and determined how many of them can support HD broadcasts?
Really? Honestly???
31 August 2008
Field Strip And Reassemble An AR-15 In 53 Seconds
26 August 2008
Reading List #8
In no particular order:
- Anything graph-related at xkcd.com
- GraphJam
- INDEXED
There you have it. Data geek humor and reading habits. Now, it's time to change into my scatter plot jammers and get to bed.
24 August 2008
My Fun Weekend
15 August 2008
Apoptosis In Botnets
"The Dutch High Tech Crime Unit has arrested two brothers behind the creation of the Shadow botnet, and now intends to use the malware distribution engine for a good cause—Shadow will now distribute the means to eradicate its own existence."
01 August 2008
Interesting Electrical Synchronicities Today
- Our well pump died during the night. I started the dishwasher last night and my darling spouse told me this morning that we had no water. Cliff Cummings Water Service (major plug for him...he's been great to us since we bought this house) in Rutland, MA rescheduled his day and provided water from deep in the ground today. A bunch of money and replacing a pump 300 or so feet down in the ground and we have running, rusty, dirty water again.
- I watched "Car of the Future" on NOVA tonight. Love those Car Talk guys and the show was actually pretty good, given what I expected for Detroit fluff. The Tesla Roadster was very nice indeed.
- Midday, iPod on shuffle, Schoolhouse Rocks! Rocks!"Electricity, Electricity" by Goodness come up. No connection until now. Fun tune and a great re-recording of the great Schoolhouse Rocks! series on PBS.
Original Schoolhouse Rocks! version:
Goodness version:
There it is...another day in the life.
25 July 2008
28 June 2008
WEIS 2008 - Day 3
A good few days all around.
27 June 2008
WEIS 2008 - Day 2
Studying Malicious Websites and the Underground Economy on the Chinese Web
Botnet Economics: Uncertainty Matters
Investigating and Prosecuting Cybercrime (Personal Favorite)
The Impact of Information Disclosure on Stock Market Returns: The Sarbanes-Oxley Act and the Role of Media as an Information Intermediary
Cyber Insurance as an Incentive for IT Security
Good stuff all around.
26 June 2008
WEIS 2008 - Day 1
Nonbanks and Risk in Retail Payments
Do Data Breach Disclosure Laws Reduce Identity Theft?
Communicating Security – The Role of Media: A Journalistic Perspective
CISO Perspective – Evaluating and Communicating Information Risk (Personal Favorite)
Communicating the Economic Value of Security Investments; Value at Security Risk
Information Governance: Flexibility and Control through Escalation and Incentives
25 June 2008
WEIS 2008 - Day 0
This year, WEIS is being hosted by the Center for Digital Strategies at the Tuck School of Business on the beautiful Dartmouth College campus in Hanover, NH.Information security requires not only technology, but a clear understanding of risks, decision-making behaviors and metrics for evaluating business and policy options. How much should we spend on security? What incentives really drive privacy decisions? What are the trade-offs that individuals, firms, and governments face when allocating resources to protect data assets? Are there good ways to distribute risks and align goals when securing information systems?
The 2008 Workshop on the Economics of Information Security, the seventh workshop, will build on a strong and growing interdisciplinary tradition, bringing together information technology academics and practitioners with social scientists and business and legal scholars to better understand security and privacy threats. Until recently, research in security and dependability focused almost exclusively on technical factors, rather than incentives. However, we know that economic, behavioral, and legal factors often contribute as much as technology to the dependability of information and information systems. The application of economic analysis to these problems has proven to be an exciting and fruitful area of research.
23 June 2008
Dymaxion Man: The Visions Of Buckminster Fuller
"Fuller’s schemes often had the hallucinatory quality associated with science fiction (or mental hospitals). It concerned him not in the least that things had always been done a certain way in the past. In addition to flying cars, he imagined mass-produced bathrooms that could be installed like refrigerators; underwater settlements that would be restocked by submarine; and floating communities that, along with all their inhabitants, would hover among the clouds. Most famously, he dreamed up the geodesic dome."
Will The Big Mac Follow Moore's Law?
"In January 2002, years before the Mega Mac introduction, Takeshi Fukuda and his friends presciently speculated on what MacDonald’s Japan may have up its sleeves for the future. As they added beef patties they eventually ran out of mathematical prefixes and began to resort to Marx Brothers references."
Original blog post by Takeshi Fukuda in Japanese.
So the question is, does the evolution of the Big Mac to Mega Mac to Tera Mac to Yotta Mac follow an 18-month time period for each burger doubling?
16 June 2008
Challenges and Directions for Monitoring P2P File Sharing Networks –or– Why My Printer Received a DMCA Takedown Notice
Q: The title of your paper indicates that you received DMCA complaints for a printer, but printers can't even run P2P software. How is that possible?
Surprisingly, it is possible. We have received DMCA complaints for several printers and even a wireless access point! (Please note that these are printers directly connected to the Internet and have their own IP addresses.) This is possible because some monitoring agencies don't verify that a user reported to be sharing a file actually is sharing that file. This allows a malicious person to frame any device connected to the Internet: whether a printer, a wireless access point, or an innocent user's computer.
I wonder how long it's going to be before some clever people figure out the RIAA, MPAA, MediaSentry, MediaDefender, etc. IP address blocks and "frames" all of them for illegal file sharing?
15 June 2008
It May Be Cliché, But This Post Is About Prof. Randy Pausch
The Last Lecture Compendium print edition:
and finally his commencement address at CMU last month:
I've never attended CMU, met Pausch or personally dealt with any life-altering situation such as terminal pancreatic cancer. I'm very fortunate, with regard to the last item. I am, however, completely in awe of the way in which he has continued living his life and remaining fully engaged with his family; I can only hope that I would be strong enough to do the same. I feel his love for his three young children everyday with my own kids of similar ages. I hope he is stronger than myself and does not become overcome with grief when imagining life without them - life for the children without a father who so clearly loves them and his spouse.
Randy Pausch may have achieved his childhood dreams but there are so many of us out here who have not done so. Most of us still have the time to do so. Do you remember your dreams? Do they still matter to you? Will you help your children achieve their dreams, knowing that every moment could potentially be your last?
I will.
Space Station Could Beam Secret Quantum Codes by 2014
01 June 2008
Delhi (Day 0)
The New Delhi airport was...interesting. Local temperature was fair at 27° C. Clearing customs was efficient and easy. We were meeting a driver who was to bring us to our hotel in Noida and this is where things got interesting. We found the driver easily enough but then an ever-growing entourage (not the Jeremy Pivin type of Entourage) began "escorting" us and "helping" with out luggage. As the trek to the car attracts more and more helpers and we finally get to the car, everyone suddenly wants to be paid $20 US for their "assistance." This caught us off-guard a bit but we managed to hang onto most of our money (I only had $6 US with me!) and an hour or so later were at our hotel in Noida enjoying a few Kingfisher lagers and unwinding.
Tomorrow is a new day.
30 May 2008
I'm Leaving On A Jet Plane....
26 May 2008
Boston University Researchers Developing Sign Language Video Dictionary
Boston University doctoral student Joan Nash, who has used American Sign Language (ASL) for most of her life, is part of a team working on an interactive video project that would create a virtual sign language dictionary, allowing someone to demonstrate a sign in front of a camera and have a computer program interpret and explain its meaning. The researchers are working with a three-year, $900,000 grant from the National Science Foundation, and are currently in the early stages of the project, which involves capturing thousands of ASL signs on video. As Nash goes through the hundreds of words in English, Elizabeth Cassidy, a native ASL speaker, signs them in front of four different cameras, three in front of her and one to her right. Two of the cameras in front of her capture close-ups from different angles and one is a wider shot. The goal is to develop a database of more than 3,000 signs, with the meaning of each sign being determined by the shape of the hands, the movement of the hands and arms, and even facial expressions. Eventually, the researchers hope the technology will be used to develop a multimedia ASL dictionary to help hearing parents better communicate with deaf children and to help sign language students.
I've often wondered if groups of people who sign, say from a particular community or geographic location, have an "accent" when they sign? Can a person signing have a "twang" or a "drawl" or something akin to a Boston accent? For instance, German telegraph operators during WWII were sometimes known to have a certain "hand" or touch to their transmission that those intercepting the transmission in Bletchley Park could identify as belonging to a certain operator. Does the same stylization or accent occur in signing?
11 May 2008
F1 in Schools
This is pretty cool. All I had growing up was the Cub Scout's annual Pinewood Derby.
From the US site:
What is F1 in Schools?It's a competition for teams of three to six school children to design and manufacture miniature CO2-powered racing cars and then race them at regional, national, and international levels. Sounds simple? Not when you consider that these 11- to 18-year old kids use state-of-the-art software programs that enable them to play around with CAD (computer aided design) and CFD (computational fluid dynamics), just like real F1 designers.
Or that they have to manage the whole project from scratch, from drawing up a business plan and raising the sponsorship, to financing it through the design and manufacturing stages, to a presentation in front of a panel of preeminent judges.
.
10 May 2008
Information Security And User Education
I spent a few hours at the weekend viewing/listening to a series of presentations to accompany the launch of the Information Security Awareness Forum (ISAF) in London. I won't bore you with all the details right now but one item in particular caught my eye/ear. One of the presenters essentially said that security awareness doesn't work, a somewhat curious point to make in support of a security awareness initiative. Anyway, it's not the first time I've heard the argument and I've been mulling it over ever since. My blood having dropped just below boiling point, it's time to respond.Today I took one of those "online security awareness" things, and came away with a whole case study on How NOT To Do security awareness. I shan't name the organization concerned because my aim is not to embarrass them in any way, and it really doesn't matter - I'm sure these lessons are equally valid for many other security awareness programs.
. . .
(I cut all of the meat out for the sake of space but it's all pithy observation in support of the title of the post). . .
OK OK I'm ranting I know, but the reason is to point out that:
I cannot understand why security awareness seems to be stuck in the mold of once-a-year inform-and-test (I used to call it the "sheep dip" approach to awareness, but subsequently found out that sheep are dipped more often than most employees are made to jump through the awareness hoops!). It's high time for a new approach and some fresh ideas.
(a) with little investment and even less thought, security awareness can be done really badly;
(b) bad security awareness is unlikely to be effective, and in fact could be counterproductive;
(c) the ineffectiveness of badly designed, constructed and delivered awareness programs says nothing about the potential for well designed, well constructed and effectively delivered programs; and
(d) it really doesn't take a genuis to figure out how to improve security awareness, especially when starting from such a low base. A 20 minute team seminar about information security would have achieved so much more than this hour or two of extreme tedium. Almost ANYTHING else would have been better!
OK, that doesn't sound unreasonable, right? He seems certainly in favor of "proper" education and a continuous cycle of verification, yes? Why would I be commenting at all? Well, I'm commenting because years ago, Marcus Ranum noted in a rather pithy commentary titled, "The Six Dumbest Ideas in Computer Security", that (#5 - Educating Users):
"Penetrate and Patch" can be applied to human beings, as well as software, in the form of user education. On the surface of things, the idea of "Educating Users" seems less than dumb: education is always good. On the other hand, like "Penetrate and Patch" if it was going to work, it would have worked by now. There have been numerous interesting studies that indicate that a significant percentage of users will trade their password for a candy bar, and the Anna Kournikova worm showed us that nearly 1/2 of humanity will click on anything purporting to contain nude pictures of semi-famous females. If "Educating Users" is the strategy you plan to embark upon, you should expect to have to "patch" your users every week. That's dumb.
The real question to ask is not "can we educate our users to be better at security?" it is "why do we need to educate our users at all?" In a sense, this is another special case of "Default Permit" - why are users getting executable attachments at all? Why are users expecting to get E-mails from banks where they don't have accounts? Most of the problems that are addressable through user education are self-correcting over time. As a younger generation of workers moves into the workforce, they will come pre-installed with a healthy skepticism about phishing and social engineering.
Dealing with things like attachments and phishing is another case of "Default Permit" - our favorite dumb idea. After all, if you're letting all of your users get attachments in their E-mail you're "Default Permit"ing anything that gets sent to them. A better idea might be to simply quarantine all attachments as they come into the enterprise, delete all the executables outright, and store the few file types you decide are acceptable on a staging server where users can log in with an SSL-enabled browser (requiring a password will quash a lot of worm propagation mechanisms right away) and pull them down. There are freeware tools like MIMEDefang that can be easily harnessed to strip attachments from incoming E-mails, write them to a per-user directory, and replace the attachment in the E-mail message with a URL to the stripped attachment. Why educate your users how to cope with a problem if you can just drive a stake through the problem's heart?
When I was CEO of a small computer security start-up we didn't have a Windows system administrator. All of the employees who wanted to run Windows had to know how to install it and manage it themselves, or they didn't get hired in the first place. My prediction is that in 10 years users that need education will be out of the high-tech workforce entirely, or will be self-training at home in order to stay competitive in the job market. My guess is that this will extend to knowing not to open weird attachments from strangers.
Heh. So there it is. In a previous post, I commented on my previous role as an internal InfoSec consultant to a higher education institution. The way I tried to bridge the gap of parochial or specialized knowledge was this:
A few years ago, I led a team of network security staff at a private New England university. One thing I stressed was collaboration with peer groups, visibility to higher decision-makers and a decidedly NON-jackboot thug approach toward requests and assistance; we were to be in the business of analysis of needs (perceived and actual) and distilling them to appropriate security controls that could best support them. I doubt I was successful in this approach as my group largely functioned without mandate but I still to this day try to keep in mind a message I pushed to my staff and to the groups I met with:
I may not know much about medical imaging or financial aid records or your particular area of expertise in computer science, biology, music, etc. What I do know a bit about is data protection and security. We meet and there is a disconnect between us. What is important to you as a researcher or faculty member? What is important to me as a staff member charged with protecting you and your data?
DNA sequencing, firewalls, intellectual property...all of this reduces to knowing and working with your constituents, addressing their needs, listening to their concerns and presenting a common, organizationally based (re: consistent) to risk management and data protection that the groups you ultimately serve can do so in a consistent manner while (hopefully) taking a risk-based approach to assessment, mitigation and remediation.
Is there any middle ground on the topic of user education, with regard to information security concerns? Is it black or white like Hinson or Ranum argue or is there some middle, moderate ground that could work?
27 April 2008
We Bought A Firewall. Isn't That Good Enough?
While the topic is generally interesting to me, three paragraphs of his post are particularly interesting and germane to the information security and data protection world I play in:
"As I meet with intelligent and well-educated professionals in my community, and talk with them about how to synchronize calendar information from a variety of sources, I realize that they simply have no intuition about the difference between a PDF file and an ICS file that contain the same calendar information. Both are computer files, right? Both can be posted to the web, right? Both can be searched, right? Problem solved.
. . .
These are ways of computational thinking unknown to most people. As a school administrator, librarian, city planner, social worker, or retail store owner, nobody expects you to understand and apply these principles.
And yet almost everybody needs to harmonize personal and organizational calendars. And many individuals and organizations need to flow their calendar data into other contexts to promote and coordinate their activities. "
If you substitute file formats for security controls and calendars for security-related procedures, I feel that the same three paragraphs capture the essence of the reason we still have phishing and spam problems, botnets, etc.: people not involved in "the trade" simply do not have the proper background nor the mindset to think properly about data protection.
Sure, some people and organizations may buy themselves a firewall and antivirus software and may ask, "We just bought a firewall. Isn't that good enough?" The answer, clearly, is "more than likely not." And this should never be presented or perceived as simply a push or a bait-and-switch attempt to push more security products or controls - the need for those elements comes from stated organizational objectives and/or policies and detailed risk analysis where the spend on security and protection controls is aligned with the value of assets being protected.
Who is qualified to make these assessments? How many people or groups are qualified (identification and selection, implementation, on-going maintenance, etc.) to handle major electrical, plumbing or construction work in their home or offices? Bad choices could easily lead to bad happenings, to put it rather simply. Viewed through a similar prism we can ask how many people or groups are qualified to properly assess risk to whatever they're trying to protect or hide or what have you? Same general answer: bad choices easily could lead to bad happenings.
Now, my comments emphasis a specialization or expertise necessary to make intelligent data security and protections decisions. We're all interested in protecting our data or at least assuming the firms we interact with do the same but largely, both cases are not true. On the individual side, a majority or people are willing to share their user IDs and passwords with strangers for a chocolate bar and at the company level, those firms who don't see a drop in stock price (consumer confidence and willingness to spend) often do very little.
This has been a bit of a long-winded way of getting back to Jon Udell's three interesting paragraphs. A few years ago, I led a team of network security staff at a private New England university. One thing I stressed was collaboration with peer groups, visibility to higher decision-makers and a decidedly NON-jackboot thug approach toward requests and assistance; we were to be in the business of analysis of needs (perceived and actual) and distilling them to appropriate security controls that could best support them. I doubt I was successful in this approach as my group largely functioned without mandate but I still to this day try to keep in mind a message I pushed to my staff and to the groups I met with:
I may not know much about medical imaging or financial aid records or your particular area of expertise in computer science, biology, music, etc. What I do know a bit about is data protection and security. We meet and there is a disconnect between us. What is important to you as a researcher or faculty member? What is important to me as a staff member charged with protecting you and your data?
DNA sequencing, firewalls, intellectual property...all of this reduces to knowing and working with your constituents, addressing their needs, listening to their concerns and presenting a common, organizationally based (re: consistent) to risk management and data protection that the groups you ultimately serve can do so in a consistent manner while (hopefully) taking a risk-based approach to assessment, mitigation and remediation.
01 April 2008
Google Gears, Part 1
Do I care? Sort of.
When you consider some other Google properties - Blogger, YouTube, News, Book Search, Picasa - you can see how Gears starts to fit into the Google experience. Working on a blog posting? Do it on the train during your commute, it's stored in the Gears database and automatically posts to Blogger when you get an active net connection. Just capture something newsworthy, Mr. Citizen Photojournalist? Dump it from your camera to your laptop running YouTube offline and the video will be stored in the Gears database until it can sync your content with your YouTube account online. Picasa already has a thick client but there's no reason Picasa web albums could not be connected to Gears for offline work.
Interestingly, these ideas aren't what I care about. It's certainly interesting from a usability point of view and allows for greater permeance of Google in your life (if you think that's a good thing) as well as allowing one to publish their virtual lives out to the Googlesphere from anywhere, connected or not.
What I'm truly in is the security controls that are utilized to protect the Gears database and the general security architecture of Gears and all of the Google properties and tools that are becoming offline-enabled. More to follow after I do some research into this.
22 March 2008
Reading List #7
- a spoonful of J.K. Rowling
- two large dollops of Madeline L'Engle
- one jigger of C.S. Lewis
- a liberal dusting of John Milton
Mix thoroughly in a steampunk bowl with a biblical spoon until "His Dark Materials" forms.
After my previous foray into and completion of Neal Stephenson's Baroque Cycle trilogy, I was thrilled that this trilogy - a virtual trifecta of literary quality - found its way to me.
Enjoy!
04 March 2008
Another Use for Second Life

Historical Maps in Second Life
This is great. I've previously posted about some unexpected consequences SL but I think this one - a San Francisco map collector who set-up his own SL island to display his collection - is a great use of SL that (to me at least) was completely unexpected. From the MIT Technology Review:
"A new installation inside Second Life is bringing alive one of the world's largest collections of antique maps. Called the David Rumsey Maps Island (registration required), the Second Life site is San Francisco map collector David Rumsey's latest high-technology plan to share his collection with as large an audience as possible."
29 February 2008
Google Sites
I'm still trying to figure out where Gears fits into it all.
24 February 2008
Google Central (part 1)
-----
I feel that I'm turning into some sort of Google-watcher these days or have been a Google junkie without realizing it.
A couple of days ago I found an entertaining video on YouTube (how apropos) of interesting sites and places to visit in Google Earth. I recently posted about new Google search functionality and presentation options. Before that it was a brief look at Google's Android mobile phone platform. Last year I was - and will soon be again - looking at Google Trends as a potential prediction tool for the American Idol contest winner.
This is sort of interesting as it brings a set of old school (Groups - Usenet, Scholar - refereed journals, and Glossary - reference sources) content together with new school (YouTube, Blogger, Google News commentary) together in a jumble of seemingly disparate audiences through Google-branded channels. It clearly extends new school functionality (Web 2.0) into old school mediums (proto-web and Web 1.0) while trying to preserve or normalize the presentation, experience and general consumption of content and services. Through this normalization process, Google is able to preserve/build brand recognition (
Google TM That's kind of cool but it doesn't seem like a Googlesque sort of venture. Until you add other Google services. Now you have an interesting stack supplying different, but converging on, fully integrated services:
- Unified messaging and search through Gmail, Gtalk, Google SMS, GOOG-411, Grand Central and Android-powered phones - interactive communication anytime, anywhere.
- Location-specific and/or context-relative search through traditional Google search, Google Local/Maps, geo-tagged Picasa pictures, Google's Ride Finder and Transit - find anything and find a way to get to it.
- Topical information via Google Trends, Google Finance, Google SMS and storage through Google Notes and Google Docs/Spreadsheets - search for time-sensitive information through a comparative search funnel, world markets and your own content and have results presented in next-to-real-time via SMS or your personalized iGoogle hompage or Google Desktop.
- Organization and sharing/presentation through Google Personalized Search, Google Docs/Calendar, Google Notes, Google Bookmarks, various Alerts (news, SMS, calendar alerts, Blogger post alerts, etc.)
22 February 2008
Google Earth Fun
Secrets Of Google Earth
The PC World staff have some still shots of some of the highlights as well as a Google Earth placemark file you can download and import to explore on your own.
My Coffee Maker...Seg Faulted???


So it's snowing today and I'm working from home for other reasons. Isn't it nice to enjoy a cup of hot, freshly brewed coffee in the morning. It sure is...until your coffee maker decides to dump core.
Crazy.
I haven't tried it again but if I need a new unit it damned well better be able to receive SNMP traps so I can set it to brew while I'm away.
17 February 2008
Useful Kibble
- Lifehacker, "an award-winning, daily blog that features tips, shortcuts, and downloads that help you get things done smarter and more efficiently."
- Wise Bread "is a community of bloggers here to help you live large on a small budget."
- Parent Hacks "is a collaborative website that collects and publishes parents’ tips, recommendations, workarounds, and bits of wisdom – their hacks – in a single pot so we can all partake."
- Geekdad, "tech toys, science projects and other nerdy things to do with your kids."
They may not have ground-breaking news, cutting edge technology reviews or deep, theoretical insights but I always manage to extract some useful kibble from them to apply to my daily existence.
03 February 2008
Great Analysis of the World's Under-Sea Fiber Network
02 February 2008
New Google Search Features
- right- and left-handed search navigation
- keyboard shortcuts for search results
- keyword suggestions
- alternate views for search results
 I like the left-handed search navigation and was playing with the layout and widgets a bit myself last summer when playing with Google's Web Toolkit. eBay has been doing some very similar UI work in its eBay Playground site that I've enjoyed. Amazon tends to overwhelm me at times with JSON this and AJAX that and they can't seem to resist the urge to package the search results and product descriptions to the extreme. I guess this shouldn't surprise me so much as they are a self-billed department store. Netflix, on the other hand, strikes the right balance with me through their consistent and concise detail drill-down through the AJAX essentials, XMLHttpRequest object and javascript onmouseover() event.
I like the left-handed search navigation and was playing with the layout and widgets a bit myself last summer when playing with Google's Web Toolkit. eBay has been doing some very similar UI work in its eBay Playground site that I've enjoyed. Amazon tends to overwhelm me at times with JSON this and AJAX that and they can't seem to resist the urge to package the search results and product descriptions to the extreme. I guess this shouldn't surprise me so much as they are a self-billed department store. Netflix, on the other hand, strikes the right balance with me through their consistent and concise detail drill-down through the AJAX essentials, XMLHttpRequest object and javascript onmouseover() event. I don't particularly care about keyboard shortcuts and search results. This is a personal inconsistency however as I don't use keyboard shortcuts in Gmail either but almost always use the keyboard to navigate between applications, tabs and the OS in general. Maybe this is my unverbalized position that I just don't like the way Google implemented keyboard shortcuts. Maybe I'm just inconsistent after all.
I don't particularly care about keyboard shortcuts and search results. This is a personal inconsistency however as I don't use keyboard shortcuts in Gmail either but almost always use the keyboard to navigate between applications, tabs and the OS in general. Maybe this is my unverbalized position that I just don't like the way Google implemented keyboard shortcuts. Maybe I'm just inconsistent after all. The keyword suggestions have been available as a Google Labs offering called Google Suggest for a while and the search bar in Firefox provides JSON-enabled search term suggestions.
The keyword suggestions have been available as a Google Labs offering called Google Suggest for a while and the search bar in Firefox provides JSON-enabled search term suggestions. The alternative search results are a great move forward with regard to search result presentation, specifically addressing the need for better contextual-based and grouped/ordered search results. I've written about this previously and was eager for new search primitives to address this perceived shortcoming or at minimum search options that accomplished the same thing.
The alternative search results are a great move forward with regard to search result presentation, specifically addressing the need for better contextual-based and grouped/ordered search results. I've written about this previously and was eager for new search primitives to address this perceived shortcoming or at minimum search options that accomplished the same thing.At least I'm not alone in liking the latest search presentation options. Ars Technica described it simply as "awesome".
14 January 2008
A Brave, New Semester
I'm hoping for a less strenuous semester than last.